If you’re using smart home devices, you probably added them to make life easier—not to worry about security. Smart lights, cameras, speakers, TVs, and plugs are supposed to feel helpful and safe. But many people don’t realize this until something goes wrong: most smart homes aren’t attacked because they’re advanced—they’re attacked because they’re set up casually.
I’ve noticed that smart home security problems usually don’t come from complicated hacking. They happen because of small things that are easy to overlook—default passwords that never got changed, Wi-Fi settings left open, software updates ignored, or features enabled that no one actually uses. These small gaps are exactly what attackers look for, and unfortunately, most homeowners never know those gaps exist.
That’s why I put this guide together on how to secure smart home devices. My goal isn’t to scare you or overwhelm you with technical terms. I want to help you understand what really puts smart homes at risk—and more importantly, how to fix it in a simple, practical way. You don’t need to be tech-savvy, and you don’t need expensive tools. You just need the right awareness and a few smart habits.
This guide is for anyone using smart home devices who wants clear, practical advice—without technical jargon or unnecessary tools.
I’m not the only one saying this. According to cybersecurity research, a large percentage of smart device breaches happen not because of advanced hacking, but because devices are left misconfigured or unsecured during setup. That’s exactly why focusing on basics makes such a big difference.
In this guide, I’ll walk you through clear, step-by-step actions to secure your home Wi-Fi, protect your smart devices from unauthorized access, reduce privacy risks, and avoid the common setup mistakes most people make. By the end, you’ll know exactly what to check, what to change, and how to use your smart home with more confidence.
Smart homes are becoming part of everyday life. And as more devices connect to your home network, taking smart home security seriously isn’t optional anymore—it’s responsible. This guide is here to help you do that, without stress and without guesswork.
If you’re facing other tech-related issues beyond smart home security, I’ve also created a dedicated Troubleshooting Guides section where I break down common tech problems into simple, actionable solutions. From fixing connectivity issues and device errors to improving performance and security, these guides are designed to help you diagnose problems quickly and resolve them without confusion.
What Are Smart Home Devices and Why Are They Vulnerable?
When I talk about smart home devices, I’m referring to any device in your home that connects to the internet to work automatically or remotely. This includes smart TVs, security cameras, doorbells, speakers, smart plugs, lights, thermostats, routers, and even appliances like washing machines or air conditioners. If a device connects to Wi-Fi and can be controlled through an app, voice command, or cloud service, it qualifies as a smart or IoT (Internet of Things) device.
The problem isn’t that these devices are “bad” or poorly designed. The real issue is how they connect to the internet.
How internet connectivity creates attack surfaces
Every time a smart device connects to your home network, it creates what security experts call an attack surface. That simply means a new entry point that could be misused if it isn’t properly secured. These devices often communicate with cloud servers, mobile apps, and other devices inside your home. If even one of those connections is weak, it can be exploited.
Many smart devices are designed for ease of use, not security-first setup. Default passwords, open ports, outdated firmware, and unnecessary features like remote access or voice control are often enabled from day one. If these settings are never reviewed, the device stays exposed.
Why attackers target home networks
Attackers don’t usually target homes because of who you are. They target home networks because they’re easy. Unlike businesses, most home networks don’t have dedicated security monitoring, firewalls, or strict access rules. Attackers know that many people never change default settings or regularly update devices, which makes automated attacks extremely effective.
Once an attacker gets into a home network, they don’t just look at one device. They explore everything connected to it.
One weak device can put your entire network at risk

This is the most important thing to understand: smart home security is only as strong as the weakest device on your network. A single unsecured smart plug, camera, or outdated router can become the entry point that exposes everything else—your phones, laptops, personal data, and other smart devices.
That’s why securing smart home devices isn’t about fixing one product. It’s about protecting the entire ecosystem inside your home. In the next sections, I’ll walk through practical steps that focus on closing these common gaps and reducing risk in a way that actually works in real homes.
Many smart home security issues don’t come from advanced hacking techniques. Consumer cybersecurity guidance consistently points out that weak passwords, outdated software, and unsecured home networks are among the most common reasons smart devices get compromised. That’s why focusing on basic setup and ongoing maintenance makes such a big difference.
Common Smart Home Security and Privacy Concerns You Should Know
When people think about smart home risks, they often imagine complex hacking or advanced cyberattacks. In reality, most problems come from basic security and privacy oversights that are easy to miss during setup.
Over time, I’ve noticed that most smart home security problems don’t come from advanced hacking, but from simple setup decisions that were never revisited.
I want to break these down clearly, so you know exactly what to watch out for—and why they matter.
Weak or Default Passwords
This is one of the most common and most dangerous issues I see. Many smart devices come with default usernames and passwords like “admin/admin,” and a surprising number of people never change them. Attackers already know these defaults, and automated tools constantly scan the internet looking for devices that still use them.
Even worse, some people reuse the same password across multiple smart devices or apps. If one device gets compromised, everything connected to it becomes vulnerable. Strong, unique passwords aren’t optional for smart homes—they’re foundational.
Insecure Home Wi-Fi Networks
Your home Wi-Fi network is the backbone of your smart home. If it’s not secure, none of your devices are truly protected. Common problems include outdated router firmware, weak Wi-Fi passwords, old encryption standards, or leaving guest networks open without restrictions.
Attackers don’t need to break into each device individually. If they gain access to your Wi-Fi network, they can scan, monitor, and interact with everything connected to it. That’s why securing your router and network settings is one of the most important steps in smart home security.
Outdated Firmware and Software
Smart devices rely on firmware and software updates to fix bugs and close security gaps. When updates are ignored or delayed, known vulnerabilities stay open—sometimes for months or even years.
What makes this risky is that attackers often exploit publicly known flaws. Once a vulnerability is discovered, it doesn’t stay secret for long. Keeping devices updated is one of the easiest ways to reduce risk, yet it’s one of the most commonly skipped steps.
Excessive App Permissions and Data Collection
Many smart home apps request more permissions than they actually need. Access to microphones, cameras, contacts, location data, or continuous background activity can create privacy risks if those permissions aren’t reviewed.
Over time, these apps may collect large amounts of personal data—sometimes more than users realize. If privacy settings are left unchecked, you may be sharing far more information than intended, even when you’re not actively using the device.
Cloud Account and Privacy Risks
Most smart home devices rely on cloud accounts to function. This means your data—video footage, voice commands, usage patterns, and device activity—is often stored on external servers.
If your cloud account is compromised due to a weak password or lack of two-factor authentication, attackers may gain access without ever touching your physical devices. Even when accounts aren’t hacked, privacy risks still exist if data retention settings and sharing options aren’t properly configured.
Understanding these concerns is the first step toward fixing them. In the next section, I’ll start walking you through practical, real-world steps you can take to secure your smart home devices and reduce both security and privacy risks in a meaningful way.
How to Secure Smart Home Devices Step by Step
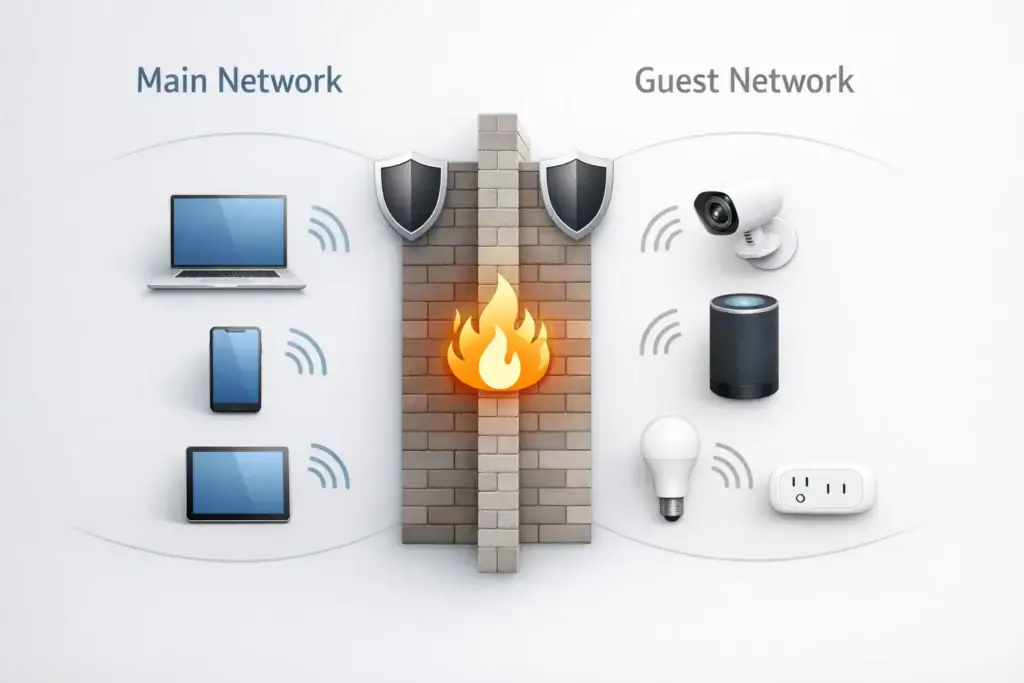
When it comes to smart home security, I always start with one rule: if your network isn’t secure, your devices aren’t either. Before worrying about individual gadgets, you need to lock down the system that connects everything together. That system is your home Wi-Fi network.
First Step: Secure Your Home Wi-Fi Network First
Your router is the gateway to your smart home. Every device—cameras, TVs, speakers, lights, plugs—depends on it. If someone gains access to your Wi-Fi network, they can potentially see, scan, or interact with everything connected to it.
Here’s how I recommend securing your home network properly.
Router security basics
Start by logging into your router’s admin panel and checking the basic settings. Many routers still use default admin usernames and passwords, which should be changed immediately. If an attacker can access your router, they don’t need to hack individual devices—they control the network.
Also, make sure remote management is disabled unless you absolutely need it. Leaving router management open to the internet creates unnecessary exposure.
Use modern Wi-Fi encryption standards
Always use WPA2 or WPA3 encryption for your Wi-Fi network. Older standards like WEP or open networks are no longer considered secure and can be broken easily. If your router supports WPA3, enable it. If not, WPA2 is still acceptable when configured with a strong password.
Encryption ensures that data moving between your devices and the router can’t be easily intercepted.
Set strong router credentials
Your Wi-Fi password should be long, unique, and not reused anywhere else. Avoid common phrases, names, or simple patterns. A strong router password is your first line of defense against unauthorized access.
If your router allows it, also change the default network name (SSID). Avoid names that reveal your router brand or model, as that information can help attackers target known vulnerabilities.
Use guest networks for smart devices
One of the smartest ways to reduce risk is to separate smart home devices from your main devices. Most modern routers allow you to create a guest network. I recommend connecting smart devices to this guest network while keeping your phones, laptops, and personal devices on your primary network.
This way, even if a smart device is compromised, it limits how far an attacker can move inside your home network. It’s a simple step that dramatically improves security.
Securing your home Wi-Fi network lays the foundation for everything else. Once your network is protected, it becomes much easier to secure individual smart devices without constantly worrying about exposure from the inside.
Step 2: Use Strong, Unique Passwords for All Smart Devices
After securing your home Wi-Fi, the next most important step is protecting each device with strong, unique passwords. This is where many smart home setups quietly fail—not because people ignore security, but because password reuse feels convenient.
Why password reuse is dangerous
Reusing the same password across multiple smart devices or apps creates a chain reaction. If just one device or account is compromised, attackers can try that same password everywhere else. In a smart home environment, that often means access to cameras, speakers, TVs, and even your router within minutes.
Attackers don’t guess passwords manually anymore. They rely on automated attacks that test known or leaked passwords across thousands of devices. Reusing passwords makes those attacks far more effective.
Device accounts vs app accounts
Smart home security isn’t just about the physical device—it’s also about the accounts behind it. Many devices require:
- A device-level login (for the device itself)
- A mobile app account
- Sometimes a cloud-based web account
Each of these layers needs its own protection. A strong password on the device won’t help if the app account uses a weak or reused password. Likewise, securing only the app while ignoring device-level credentials still leaves an opening.
I always recommend treating every login—device, app, and cloud account—as a separate entry point that needs its own password.
Best practices for creating strong passwords
Strong passwords don’t need to be complicated, but they do need to be unique and hard to guess. I suggest using long passphrases instead of short, complex strings. Avoid personal details, device names, or anything easily associated with you.
Most importantly, never leave default passwords unchanged. Default credentials are publicly known and actively targeted. Changing them immediately blocks a large percentage of basic attacks.
Securing smart devices with strong, unique passwords might feel like extra effort upfront, but it dramatically reduces risk. It’s one of the simplest steps you can take to protect your smart home and maintain long-term security.
Step 3: Enable Two-Factor Authentication to Prevent Unauthorized Access
Strong passwords are essential, but on their own, they’re not always enough. That’s where two-factor authentication (2FA) makes a big difference, especially when you’re trying to protect smart home devices from hackers.
What two-factor authentication protects against
Two-factor authentication adds an extra verification step when someone tries to log in to a device or account. Even if an attacker somehow gets your password—through a data breach, phishing, or password reuse—they still can’t access your account without the second factor. This could be a one-time code, an app confirmation, or a hardware-based prompt.
For smart home setups, 2FA is most important on:
- Your router or network admin account
- Smart home hub apps
- Cloud accounts linked to cameras, doorbells, and voice assistants
These accounts control multiple devices at once, so securing them has a big impact.
How 2FA blocks common attacks
Most smart home breaches don’t involve sophisticated techniques. They rely on stolen or guessed passwords. Two-factor authentication stops these attacks cold by requiring something the attacker doesn’t have.
Even if login details are exposed online, 2FA prevents attackers from signing in remotely. In many cases, it also alerts you to suspicious login attempts, giving you a chance to act before any damage is done.
Enabling two-factor authentication wherever it’s available is one of the most effective ways to protect smart home devices from unauthorized access. It turns a single point of failure into a layered defense—and that’s exactly what smart home security needs.
Step 4: Keep Smart Home Devices and Apps Updated
One of the easiest ways to improve smart device security is also one of the most commonly ignored: keeping devices and apps up to date. Updates may seem minor or inconvenient, but they play a critical role in protecting smart home systems.
Why updates matter for smart devices
Smart home devices rely on firmware and software to function securely. When security flaws are discovered, manufacturers release updates to fix them. If those updates aren’t installed, the device remains exposed to vulnerabilities that attackers already know about.
What makes this risky is that many attacks target known weaknesses, not unknown ones. Once a vulnerability becomes public, it can be exploited quickly. Regular updates close these gaps, improve stability, and often enhance privacy controls as well.
Auto-update pros and cons
Enabling automatic updates is usually the safest option, especially if you don’t want to manually check every device. Auto-updates ensure critical security fixes are applied as soon as they’re available, reducing the window of exposure.
However, automatic updates can occasionally cause temporary issues, such as changes in settings or compatibility. That’s why I recommend enabling auto-updates where possible, but also reviewing update notes occasionally—especially for major devices like routers, cameras, or smart hubs.
Keeping smart home devices and their apps updated doesn’t require technical expertise. It just requires consistency. Over time, this simple habit significantly strengthens smart device security and reduces long-term risk.
Step 5: Limit Features and App Permissions You Don’t Use
When it comes to smart home protection, security isn’t just about keeping attackers out—it’s also about limiting how much access devices and apps have in the first place. Many smart home devices work perfectly fine with only a fraction of their available features enabled.
Microphone, camera, and location access
Smart home apps often request access to microphones, cameras, location data, and background activity. Sometimes this access is necessary, but often it isn’t. Leaving these permissions enabled all the time increases privacy risks and expands the potential attack surface.
For example, a smart speaker doesn’t need constant microphone access when it’s not in use, and a smart camera may not need continuous cloud access if local controls are available. Location tracking is another permission that’s frequently enabled by default, even when it’s not required for core functionality.
Why fewer permissions mean less risk
Every enabled feature is another doorway into your smart home ecosystem. The more doors you leave open, the easier it is for something to go wrong—whether that’s unauthorized access, data collection, or accidental exposure.
Limiting permissions reduces the amount of data your devices can collect and share, and it minimizes the damage if a device or account is compromised. This kind of awareness-driven approach to smart home security is often overlooked, but it’s one of the simplest ways to improve protection without adding complexity.
Taking a few minutes to review and disable unused features helps you stay in control of your devices—and your privacy.
How to Secure Smart Home Devices on Your Network
When people ask me how to secure smart home devices, I always bring the conversation back to one thing: the network. You can lock down individual devices as much as you want, but if everything is sitting on the same open network, one weak point can still expose the rest.
Network-level security is what turns a collection of smart gadgets into a safer system.
Why network-level security is critical
All smart home devices communicate through your home network. Cameras, TVs, speakers, plugs, and hubs constantly send and receive data—often at the same time as your phones, laptops, and personal devices.
If an attacker gains access to your network, they don’t need to break into each device individually. They can scan what’s connected, move laterally, and look for easier targets. That’s why securing devices without thinking about the network leaves a major gap.
Isolating smart devices from personal devices
One of the most effective ways to protect your home is to separate smart devices from your primary devices. Your phone, laptop, and work systems likely contain far more sensitive information than a smart bulb or plug. They shouldn’t be exposed to the same risks.
By isolating smart devices on a separate network, you limit how far an attacker can go if one device is compromised. Instead of gaining access to everything, the damage is contained.
Guest networks explained simply

Most modern routers offer a guest network feature. While it’s often used for visitors, it works extremely well for smart home devices.
Here’s the simple idea:
- Your main network is for phones, computers, and personal data
- The guest network is for smart devices that don’t need access to your private files
Devices on the guest network can still connect to the internet and function normally, but they can’t easily interact with devices on your main network. This separation adds a powerful layer of protection without any complicated setup.
How this reduces damage if one device is hacked
No smart home setup is 100% risk-free. Devices can have bugs, updates can be delayed, and mistakes happen. Network segmentation is important because it assumes that something might go wrong—and prepares for it.
If a smart device is compromised while isolated on a separate network, the attacker’s access is limited. Your personal devices, sensitive data, and other systems stay protected. Instead of a full-network breach, you’re dealing with a contained issue.
Securing smart home devices at the network level isn’t about paranoia—it’s about smart planning. It’s one of the most practical steps you can take to protect your home without adding complexity or stress.
How to Secure Smart Home Devices from Hacking and Cyber Attacks
When people hear the word “hacking,” it often sounds dramatic or overly technical. In reality, most cyber attacks on smart home devices are simple, automated, and avoidable. Understanding how these attacks happen makes it much easier to prevent them—without panic or fear.
Common hacking techniques (explained simply)
Most attackers don’t target individuals personally. They use automated tools that scan thousands of home networks and devices looking for easy entry points. These tools check for things like default passwords, weak Wi-Fi security, outdated software, and open remote access features.
If a device responds in a way that suggests it’s poorly secured, the attack continues. If not, the attacker moves on. This is why basic security steps stop the majority of attacks before they even begin.
How attackers exploit weak setups
Attackers take advantage of convenience-driven setups. Devices that are installed quickly and never reviewed tend to have:
- Default or reused passwords
- Outdated firmware
- Unrestricted network access
- Excessive app permissions
Once one device is exposed, attackers often try to move deeper into the network. They don’t need advanced skills—just a weak configuration to work with.
Prevention mindset, not panic
The most important thing I want to emphasize is this: smart home security is about prevention, not panic. You don’t need to constantly monitor your devices or worry about worst-case scenarios. Most risks can be reduced dramatically by focusing on a few consistent habits—securing your network, updating devices, limiting permissions, and using layered protection like two-factor authentication.
When you approach smart home security with awareness instead of fear, you gain control. And once the basics are in place, your smart home becomes far less attractive to attackers looking for easy targets.
How to Monitor Smart Home Devices for Suspicious Activity
Securing smart home devices isn’t a one-time setup—it’s an ongoing process. Even with strong passwords, updates, and network protection in place, it’s important to pay attention to how your devices behave over time. Monitoring doesn’t mean constant checking; it means knowing what looks normal so you can spot what doesn’t.
Warning signs a smart device may be compromised
Most smart home issues don’t announce themselves loudly. Instead, they show up as small changes that are easy to ignore. Some common warning signs include:
- Devices turning on or off unexpectedly
- Settings changing without your input
- Slow or unstable performance after working fine before
- Repeated login alerts or unfamiliar access notifications
- Cameras or microphones activating when they shouldn’t
One sign alone doesn’t always mean a device is hacked, but patterns matter. If something feels off and you didn’t make the change, it’s worth investigating.
Router activity awareness matters more than you think
Your router is the best place to monitor what’s happening on your home network. Most routers allow you to see a list of connected devices. I recommend checking this occasionally to make sure everything looks familiar.
Look out for:
- Unknown device names
- Devices connected at unusual times
- Duplicate or strangely named entries
If you see something you don’t recognize, don’t ignore it. Removing unfamiliar devices and changing your Wi-Fi password immediately can stop a potential issue from spreading.
When to reset or remove a device
Sometimes the safest option is to reset a smart device to factory settings, especially if:
- You can’t explain recent behavior
- The device hasn’t received updates in a long time
- You no longer use it or trust the manufacturer
After resetting, reconnect the device carefully using strong passwords and updated settings. If a device continues to behave unpredictably or no longer receives security updates, it may be better to remove it from your network entirely.
Monitoring smart home devices isn’t about suspicion—it’s about awareness. A few quick checks from time to time can help you catch problems early and keep your smart home secure without added stress.
Common Smart Home Security Mistakes to Avoid
Even with the best intentions, many smart home security problems happen because of small, everyday mistakes. These issues are common, understandable, and often easy to fix once you’re aware of them. Avoiding these mistakes is a big part of following smart home security best practices.
Leaving default settings unchanged
One of the biggest mistakes is setting up a smart device and never revisiting its settings. Default usernames, passwords, device names, and permissions are designed for quick setup—not long-term security.
Leaving these defaults in place makes devices predictable and easier to target. Taking a few minutes to review and customize settings immediately reduces risk and improves overall protection.
Ignoring updates
Skipping updates doesn’t just delay new features—it leaves known security weaknesses open. Many people ignore update notifications because devices appear to be working fine. Unfortunately, attackers rely on this exact behavior.
Regular updates close vulnerabilities that attackers actively look for. Ignoring them increases exposure over time, especially as devices age.
Connecting everything to one network
Putting all devices—smart devices, phones, laptops, and work systems—on a single network creates unnecessary risk. If one device is compromised, everything else becomes reachable.
Separating smart devices onto a guest or secondary network limits how far an attacker can go. This simple step is one of the most effective ways to contain damage.
Buying devices without security research
Not all smart devices are equal when it comes to security. Some manufacturers provide regular updates and long-term support, while others stop updating products shortly after release.
Before buying a smart device, it’s important to check whether the manufacturer has a history of security updates and clear privacy policies. Choosing devices with ongoing support is a key part of long-term smart home security.
Avoiding these common mistakes doesn’t require advanced knowledge—just awareness. Small decisions made during setup and purchasing can make a big difference in how secure your smart home remains.
How Secure Is a Smart Home Really?
This is one of the most common questions people ask—and the honest answer is: a smart home is only as secure as the way it’s set up and maintained. Smart homes aren’t automatically insecure, but they aren’t automatically safe either.
Security depends on how devices are configured
Smart home security isn’t determined by how many devices you own or how advanced they are. It depends on basics like network protection, password strength, updates, and account security. A home with several smart devices can be far safer than a home with only one poorly configured device.
Most security issues don’t come from the technology itself—they come from weak setups, ignored updates, or reused credentials. When those gaps are addressed, the risk drops significantly.
Smart homes can be safe with proper practices
When smart home devices are set up thoughtfully, they can be just as secure as any other connected system. Strong passwords, two-factor authentication, network segmentation, limited permissions, and regular monitoring all work together to reduce risk.
The key is consistency. Smart home security isn’t about doing everything perfectly once; it’s about maintaining good habits over time. With the right practices in place, smart homes can be both convenient and secure—without constant worry or technical complexity.
Also Read These Related Articles:
- How to Integrate All Smart Home Devices: Your Ultimate Guide
- 10 Ways Smart Home Devices Will Transform Your Life
- Top 10 Best Smart Home Devices You Can’t Miss Right Now
- The Ultimate Guide to Setting Up Your Home Office Tech
Conclusion: Building a Secure Smart Home Through Awareness and Good Habits
Securing a smart home isn’t about chasing perfection or using complicated tools—it’s about awareness and consistency. Most smart home security issues don’t happen because people ignore safety altogether. They happen because small details are overlooked over time.
What makes the biggest difference is understanding how your devices connect, what access they have, and how they’re maintained. Simple habits—like securing your network, using unique passwords, enabling two-factor authentication, keeping devices updated, and reviewing permissions—reduce risk far more effectively than relying on any single feature or product.
Smart home security is an ongoing process, not a one-time setup. Devices change, software updates roll out, and new technology enters your home. Staying aware and making small adjustments along the way helps you stay in control without added stress.
With the right habits in place, a smart home can be both convenient and secure. Awareness, not fear, is what ultimately keeps your smart home protected.
By now, you’ve seen that securing smart home devices isn’t about fear or complexity—it’s about awareness, consistency, and smart setup choices. Below, I’ve answered some common questions people still have when securing their smart homes.
Frequently Asked Questions About Smart Home Security
This section answers some of the most common questions people ask when trying to understand and improve smart home security. These answers are written clearly and practically, so you can apply them right away.
What is the best smart home security?
The best smart home security doesn’t come from a single device or product. It comes from layered protection. This includes a secure home Wi-Fi network, strong and unique passwords, two-factor authentication, regular updates, limited app permissions, and basic monitoring.
When these elements work together, they significantly reduce risk. Smart home security is most effective when it’s built into daily habits rather than relying on one solution alone.
What are the privacy issues with smart home devices?
Smart home devices often collect data such as voice commands, video recordings, usage patterns, and location information. Privacy issues usually arise when apps have excessive permissions, data-sharing settings are left unchecked, or cloud accounts are not properly secured.
Reviewing privacy settings, disabling unused features like microphones or cameras, and securing cloud accounts with strong passwords and two-factor authentication can greatly reduce privacy risks.
How secure is a smart home?
A smart home can be very secure—or very vulnerable—depending on how it’s set up. Devices themselves are not inherently unsafe, but weak configurations such as default passwords, outdated software, or unsecured networks increase risk.
With proper setup and ongoing maintenance, smart homes can be just as secure as traditional home networks while offering far more convenience.
What is the best way to secure a home Wi-Fi network?
The best way to secure your home Wi-Fi network is to start with your router. Change default login credentials, use strong Wi-Fi passwords, enable WPA2 or WPA3 encryption, and keep router firmware updated.
Using a guest network for smart home devices and keeping personal devices on a separate network adds another important layer of protection.
How do you secure IoT devices at home?
To secure IoT devices at home, focus on the basics:
Change default passwords immediately
Use strong, unique passwords for each device and app
Enable two-factor authentication where available
Keep firmware and apps updated
Limit permissions and disable unused features
Monitor connected devices periodically
These steps work together to reduce exposure and protect your entire home network.
If you found this guide helpful, I’d genuinely love to hear your thoughts. Feel free to leave a comment below and share what you found most useful or if there’s a specific smart home issue you’re dealing with right now. I also share practical tech tips, troubleshooting guides, and security insights regularly, so if you’d like more content like this, you can subscribe to the email newsletter and stay updated without any noise or spam.

𝐈’𝐦 𝐒𝐭𝐞𝐯𝐞 𝐇𝐨𝐮𝐠𝐚𝐧, the writer and researcher 𝐛𝐞𝐡𝐢𝐧𝐝 𝐔𝐒𝐀 𝐓𝐞𝐜𝐡 𝐃𝐞𝐚𝐥𝐬.
I help everyday users understand technology—𝐰𝐡𝐞𝐭𝐡𝐞𝐫 𝐢𝐭’𝐬 𝐜𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐭𝐡𝐞 𝐫𝐢𝐠𝐡𝐭 𝐝𝐞𝐯𝐢𝐜𝐞, 𝐝𝐢𝐚𝐠𝐧𝐨𝐬𝐢𝐧𝐠 𝐩𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞 𝐢𝐬𝐬𝐮𝐞𝐬, 𝐬𝐞𝐭𝐭𝐢𝐧𝐠 𝐮𝐩 𝐡𝐨𝐦𝐞-𝐨𝐟𝐟𝐢𝐜𝐞 𝐞𝐪𝐮𝐢𝐩𝐦𝐞𝐧𝐭, 𝐨𝐫 𝐬𝐨𝐥𝐯𝐢𝐧𝐠 𝐜𝐨𝐦𝐦𝐨𝐧 𝐭𝐞𝐜𝐡 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬.
My content blends deep research, expert-backed insights, and real user feedback to bring you clear, practical, and easy-to-follow guidance. 𝐈 𝐚𝐧𝐚𝐥𝐲𝐳𝐞 𝐩𝐫𝐨𝐝𝐮𝐜𝐭𝐬, 𝐜𝐨𝐦𝐩𝐚𝐫𝐞 𝐟𝐞𝐚𝐭𝐮𝐫𝐞𝐬, 𝐬𝐭𝐮𝐝𝐲 𝐭𝐞𝐜𝐡𝐧𝐢𝐜𝐚𝐥 𝐬𝐩𝐞𝐜𝐢𝐟𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬, 𝐞𝐱𝐩𝐥𝐨𝐫𝐞 𝐭𝐫𝐨𝐮𝐛𝐥𝐞𝐬𝐡𝐨𝐨𝐭𝐢𝐧𝐠 𝐦𝐞𝐭𝐡𝐨𝐝𝐬, 𝐚𝐧𝐝 𝐛𝐫𝐞𝐚𝐤 𝐝𝐨𝐰𝐧 𝐜𝐨𝐦𝐩𝐥𝐞𝐱 𝐭𝐞𝐜𝐡 𝐭𝐨𝐩𝐢𝐜𝐬 𝐢𝐧𝐭𝐨 𝐬𝐢𝐦𝐩𝐥𝐞, 𝐚𝐜𝐭𝐢𝐨𝐧𝐚𝐛𝐥𝐞 𝐬𝐭𝐞𝐩𝐬.
𝐇𝐞𝐫𝐞 𝐨𝐧 𝐔𝐒𝐀 𝐓𝐞𝐜𝐡 𝐃𝐞𝐚𝐥𝐬, 𝐲𝐨𝐮’𝐥𝐥 𝐟𝐢𝐧𝐝:
Tech buying guides based on verified data and side-by-side comparisons
Product insights that highlight pros, cons, and real-world use cases
Step-by-step tutorials for fixing, optimizing, and understanding devices
Home-office and productivity setup advice
Educational articles that simplify complicated tech concepts
Video explanations featuring me as your on-screen tech guide
𝐌𝐲 𝐦𝐢𝐬𝐬𝐢𝐨𝐧 𝐢𝐬 𝐭𝐨 𝐡𝐞𝐥𝐩 𝐲𝐨𝐮 𝐦𝐚𝐤𝐞 𝐬𝐦𝐚𝐫𝐭𝐞𝐫 𝐝𝐞𝐜𝐢𝐬𝐢𝐨𝐧𝐬, 𝐚𝐯𝐨𝐢𝐝 𝐦𝐢𝐬𝐭𝐚𝐤𝐞𝐬, 𝐬𝐨𝐥𝐯𝐞 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬 𝐟𝐚𝐬𝐭𝐞𝐫, 𝐚𝐧𝐝 𝐠𝐞𝐭 𝐭𝐡𝐞 𝐦𝐨𝐬𝐭 𝐨𝐮𝐭 𝐨𝐟 𝐲𝐨𝐮𝐫 𝐝𝐞𝐯𝐢𝐜𝐞𝐬—𝐰𝐢𝐭𝐡𝐨𝐮𝐭 𝐜𝐨𝐧𝐟𝐮𝐬𝐢𝐨𝐧 𝐨𝐫 𝐨𝐯𝐞𝐫𝐰𝐡𝐞𝐥𝐦.
Stay connected for helpful guides, latest tech insights, and smart recommendations.
Follow us on: YouTube • Instagram • Facebook • X (Twitter) • LinkedIn • Pinterest • TikTok